Tackling a Big History Lie Fueling Putin’s Xi-Jinping-Aided Aggression
Despite Beijing’s global posturing in support of national sovereignty it uses sleight of hand to export “dual use” technology (civilian and military) to supply Putin’s war of aggression against Ukraine’s sovereignty. Yet Ukraine’s sovereignty is a matter of widespread international recognition. China’s strategy seems simple: tax Ukraine and the West to the point that it…
SOCMINT Sample: Putin’s Strategic Disinformation
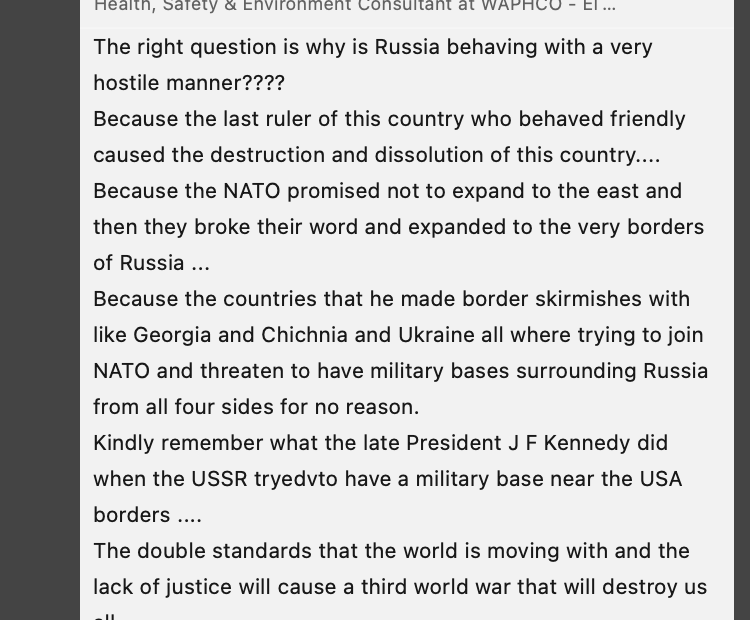
Putin regime proxy profiles (paid, voluntary, or unwitting) are alleging Russian active measures talking points that the Putin dictatorship’s attacking Ukraine is only doing what John F. Kennedy did during the Cuban Missile Crisis and or the Bay of Pigs invasion. This narrative is false in a number of ways: 1. False Analogy as…
Privacy-as-Security
Privacy and national security are in a form of quantum entanglement over the internet. Stratpass Corp defined the issue five years ago in terms of “Privacy-as-Security,” and centering on the need for greater legal power instituted in the individual right to consent, not consent, or withdraw consent to a number of things that happen to…
The January Surprise: Delusion as Inability for Trump Removal Under 25th Amendment
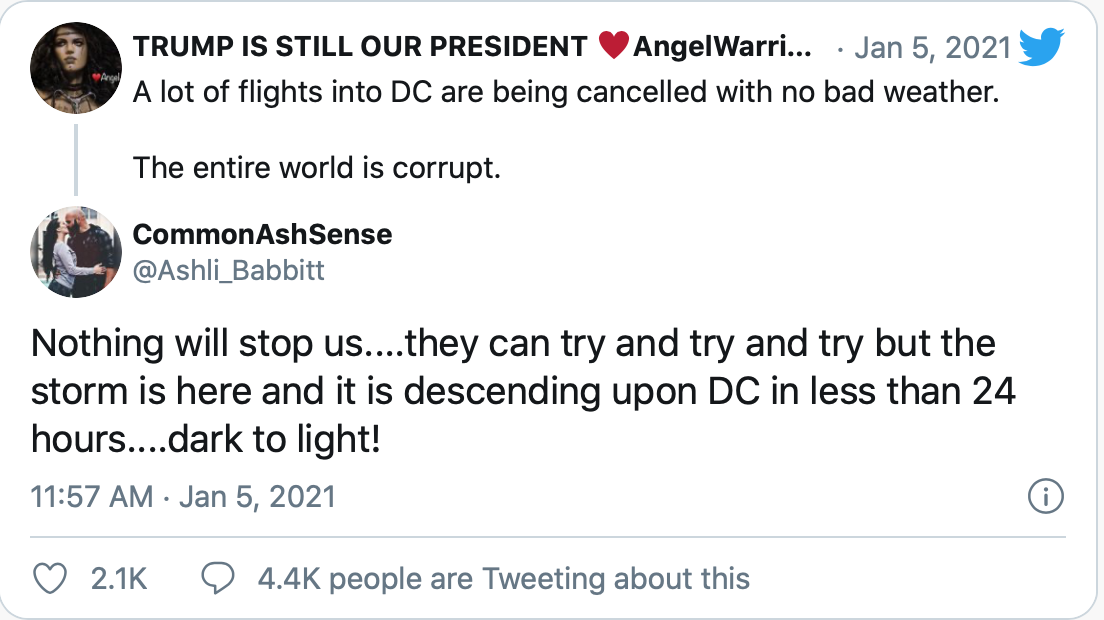
Written Summer 2019, w/ Lead Updated for Post-MAGA Storming of the U.S. Capitol, Violence, & Casualties With doublespeak for which he is well known, President Trump on January 6, 2021 incited from among a mass of his supporters, certain fanatics, personality cultists, conspiracy theorists, and opportunistic extremist groups to storm the U.S. Capitol building with…